Identity and Access Management
SAP Identity and Access Management: Identity and Access Management (IAM) is the collective name of a set of tools that allows you to manage user access to the Fiori apps and specify what users can do and see in the apps
Identity and Access Management (IAM) is the collective name of a set of tools that allows you to manage user access to the Fiori apps and specify what users can do and see in the apps.
The main elements of IAM are business catalogs, business roles, and business users. Each employee in your organization is given a business user to which you can assign business roles. The business roles contain restrictions that specify what activities are allowed and what data sets are available with each role. To each business role you can assign business catalogs that provide access to the apps.
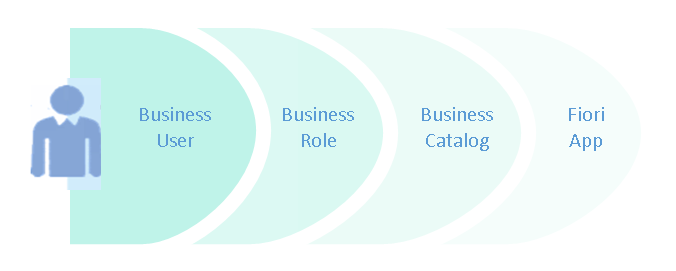
The main elements of IAM
Users don’t need to know about the access rights granted for them by IAM – when they open the launchpad, they see only those apps that are available to them. Similarly, within the apps only those data sets are visible and those commands are active that the users are authorized to see or use.
The following graphic illustrates a possible scenario in IAM:

A possible scenario in SAP Identity and Access Management
The following take place in this example:
- Two apps are assigned to a business catalog.
- Two different business roles are created based on different restrictions, but they both provide access to the same business catalog, which in turn provides access to two different apps. As a result, both business roles provide access to both Fiori apps, but different restrictions apply to them.
- Different permission filters are assigned to each business role.
- Employees are created.
- Business users are created based on the employees.
- Both business roles are assigned to one of these business users and one of the business roles is also assigned to the other business user.
- Additional permission filters are assigned to each business user.
- Both business users are assigned to the same user group.
Onboarding
To use SAP Integrated Business Planning as an administrator, you need the following:
- A customized URL to activate the administrator user and an URL for the administration console of the Identity Authentication service. This information is sent to the IT contact in the form of an activation email.
- A customized URL to log on to SAP Integrated Business Planning. This information is sent to the IT contact at your organization.
After you’ve activated your administrator user, create your employees and business users as described in User Authentication.
User Types
The user types that are required for SAP Intelligent Trade Claims Management include:
- Super administrator:
- The user who subscribes to SAP Intelligent Trade Claims Management in SAP for Me. This is the first user who is provided with access to the solution prior to any additional user setup.
- System administrator:
- Full access users for accounts that have all permissions, including account maintenance.
- Business users:
- Business users are assigned by system administrators that can edit, but can’t access settings.
Authentication and Single Sign-On
SAP Intelligent Trade Claims Management supports the Single Sign-On (SSO) mechanisms and the enhancements that improve the user experience, improve security, and simplify configuration. It assists customers who use more than one Identity Provider (like OKTA, Azure SSO, or Active Directory Federation Service) for Single Sign-On (SSO).
Identity and Authentication Architectural Overview
Identity and authentication for the solution is handled differently than many other SAP solutions. Authorization of users comes from SAP CRM and authentication is handled via a SAML connection to your corporate identity provider with SAP Identity and Authentication service functioning as a proxy to SAP Intelligent Trade Claims Management. This is depicted in the graphic below.

Conclusion
In a world where digital threats are omnipresent, SAP Identity and Access Management emerges as a formidable shield. Beyond fortifying security, it streamlines access, ensures compliance, and adapts to future challenges. Organizations willing to embrace this technology stand not just to protect their data but also to thrive in an increasingly digital landscape.
FAQs
1. How does SAP IAM enhance cybersecurity?
SAP IAM enhances cybersecurity by implementing robust authentication, authorization, and encryption measures, safeguarding against unauthorized access and potential data breaches.
2.Can small businesses benefit from SAP IAM?
Absolutely. While implementation may require adjustments, the benefits of enhanced security, streamlined access, and regulatory compliance are valuable for businesses of all sizes.
3.Are there industry-specific challenges in IAM implementation?
Yes, industries may face unique challenges, and SAP IAM solutions are often tailored to address specific needs within sectors like healthcare, finance, and manufacturing.
4.What role does user training play in the success of IAM?
User training is pivotal for successful IAM implementation. It ensures smooth adoption, minimizes resistance, and empowers employees to use the system effectively.
5.How often should organizations update their IAM systems?
Regular updates are essential to adapt to evolving threats. Organizations should schedule frequent audits and updates to keep their SAP IAM systems at peak performance.